Thanks to Christoph Murauer for an excellent guide to installing ClamAV 0.97.3 on Mac OS X!
Check out Christoph's ClamAV 0.97.3 install guide here.
Thanks to all of our ClamAV community contributors on their documentation, if you'd like to contribute some documentation, please feel free to contact me at joel@snort.org.
As always Snort.org makes no warranty or edits to submitted documentation, and we'd like to thank the contributors of the documentation for their time.
Friday, December 9, 2011
Friday, November 4, 2011
Bytecode signatures for polymorphic malware
About one year ago Alain presented the LLVM-based ClamAV bytecode. We've realised that, besides that initial introduction, we've never shown any real life use case, nor did we ever demonstrate the incredible power and flexibility of the ClamAV bytecode engine. I'll try to fix that today.
I decided to target the Xpaj virus because it's an polymorphic file infector, which means that it is not easily to detected with plain signatures.
Please note that I'm just focusing on the detection of Xpaj via bytecode signatures, not on Xpaj itself which was already thoroughly reviewed and explained.

Pic.1: Clean file

Pic.2: Same file as above, but infected with Xpaj
For the scope of this blog post, it suffices to say that Xpaj is a file infector targeting 32-bit Windows executables and DLLs which employs entry-point obfuscation (EPO) capabilities in order to make the detection harder. In particular, the virus code hijacks a few API calls in the .text section of the file, diverting them to its own routine.
This routine is located within the .text section and consists of a series of small chunks of code connected by jumps. Most of that is “garbage”. The only thing this preliminary block of code does is compute the code address for the next stage and jump to it. The actual viral code, as well as the overwritten blocks, are stored, in encrypted form, inside the data section.
Well... enough technical info already. From now on I'll just focus on the Xpaj detection, or rather, the detection of a rather simplified version of it in order to keep this blog post small and readable. The geeks can find the full source code here.
Let's start with a look at the virus entry point code:
After that we have some optional trash (do nothing) code, and then the virus saves the content of 3 random registers, which will be clobbered later by both the virus code and the trash engine too.
So far we can still get away with a signature that makes use of a wildcard, however we still don't have much: stack allocation and 3 registers saved. That's still not enough.
Next, we've got the trash engine in all its glory, and eventually we reach a function call.
The trash code may or may not jump to another chunk of code. And that effectively kills our ability to use a normal (ndb or ldb) signature.
Not all is lost, though. We can still write a small piece of bytecode signature which follows the code through the trash and checks for specific fingerprints.
In particular we plan to scan the code section for something that looks like the following:
Back outside the call we have a couple of other less interesting fingerprints and eventually the virus will jump to some runtime computed location. There are two ways by which this is achieved:
Ok let's code...
First we look for the 5 static bytes at the virus entry point (EP):
As for the actual opcode matching, here are a few examples. The first thing we are interested in is the 3 pushes. In terms of bytecode we need to check that:
I decided to target the Xpaj virus because it's an polymorphic file infector, which means that it is not easily to detected with plain signatures.
Please note that I'm just focusing on the detection of Xpaj via bytecode signatures, not on Xpaj itself which was already thoroughly reviewed and explained.
Pic.1: Clean file
Pic.2: Same file as above, but infected with Xpaj
For the scope of this blog post, it suffices to say that Xpaj is a file infector targeting 32-bit Windows executables and DLLs which employs entry-point obfuscation (EPO) capabilities in order to make the detection harder. In particular, the virus code hijacks a few API calls in the .text section of the file, diverting them to its own routine.
This routine is located within the .text section and consists of a series of small chunks of code connected by jumps. Most of that is “garbage”. The only thing this preliminary block of code does is compute the code address for the next stage and jump to it. The actual viral code, as well as the overwritten blocks, are stored, in encrypted form, inside the data section.
Well... enough technical info already. From now on I'll just focus on the Xpaj detection, or rather, the detection of a rather simplified version of it in order to keep this blog post small and readable. The geeks can find the full source code here.
Let's start with a look at the virus entry point code:
push ebpWhile these are technically enough bytes to create a signature based on the opcodes, such a signature would be a really bad idea. What we have there, in fact, is just a pretty standard function entry point.
mov ebp, esp
sub esp, XX
After that we have some optional trash (do nothing) code, and then the virus saves the content of 3 random registers, which will be clobbered later by both the virus code and the trash engine too.
So far we can still get away with a signature that makes use of a wildcard, however we still don't have much: stack allocation and 3 registers saved. That's still not enough.
Next, we've got the trash engine in all its glory, and eventually we reach a function call.
The trash code may or may not jump to another chunk of code. And that effectively kills our ability to use a normal (ndb or ldb) signature.
Not all is lost, though. We can still write a small piece of bytecode signature which follows the code through the trash and checks for specific fingerprints.
In particular we plan to scan the code section for something that looks like the following:
mov edi, ediHere we are inside "$DELTA"..
push ebp
mov ebp, esp
sub esp, $STACKSIZE
[optional trash]
push eax (*)
push edx (*)
push edi (*)
(*) note, the registers are chosen randomly among the 32 bit general purpose registers except esp and ebp
[optional trash]
call $DELTA
[optional trash]
mov register, [ebp-stacksize]
[optional trash]
ret
Back outside the call we have a couple of other less interesting fingerprints and eventually the virus will jump to some runtime computed location. There are two ways by which this is achieved:
jmp local_varor
push local_var
ret
Ok let's code...
First we look for the 5 static bytes at the virus entry point (EP):
seek(begin_of_the_code_section, SEEK_SET);Then we set ourselves in a disassembly loop and we check if we got what we expect. Something along the lines of:
cur = file_find_limit("\x55\x89\xe5\x83\xec", 5, end_of_the_code_section);
if(cur < 0) return 0;
while(1) {
struct DIS_fixed d;
int next = DisassembleAt(&d, cur, space_remaining);
if(next == -1) break; /* disasm error */
cur = next; /* cur now points at the next op */
[here we check the op]
}
As for the actual opcode matching, here are a few examples. The first thing we are interested in is the 3 pushes. In terms of bytecode we need to check that:
1. the opcode is OP_PUSH
2. the argument is a register
3. the register is one of (eax, ebx, ecx, edx, esi, edi)
In BC that'd be:
1. the opcode is a call
i.e.: d.x86_opcode == OP_CALL
2. the argument is an immediate relative value
i.e.: d.arg[0].access_type == ACCESS_REL
Then we pick the call target and we "jump" to it, not before saving the return address:
Another interesting example is the trash code parser. There can be 3 types or trash ops:
2. the argument is a register
3. the register is one of (eax, ebx, ecx, edx, esi, edi)
In BC that'd be:
d.x86_opcode == OP_PUSHAltogether:
d.arg[0].access_type == ACCESS_REG
d.arg[0].u.reg == REG_EAX || d.arg[0].u.reg == REG_ECX || d.arg[0].u.reg == REG_EDX || d.arg[0].u.reg == REG_EBX || d.arg[0].u.reg == REG_ESI || d.arg[0].u.reg == REG_EDI
if(d.x86_opcode == OP_PUSH && d.arg[0].access_type == ACCESS_REG && (d.arg[0].u.reg == REG_EAX || d.arg[0].u.reg == REG_ECX || d.arg[0].u.reg == REG_EDX || d.arg[0].u.reg == REG_EBX || d.arg[0].u.reg == REG_ESI || d.arg[0].u.reg == REG_EDI))Then we need to check for the call $DELTA. In other words we check that:
1. the opcode is a call
i.e.: d.x86_opcode == OP_CALL
2. the argument is an immediate relative value
i.e.: d.arg[0].access_type == ACCESS_REL
Then we pick the call target and we "jump" to it, not before saving the return address:
int32_t target_address, return_address;
seek(cur-4, SEEK_SET); /* we position onto the call argument */
read(&target_address, sizeof(target_address)); /* we read the relative jump value */
target_address = le32_to_host(target_address); /* we handle big endian machines */
retaddr = cur; /* we save the address to return to */
target_address = cur + target_address; /* we compute the addres to jump to */
Another interesting example is the trash code parser. There can be 3 types or trash ops:
A. Arithmetic or logic operation on a stack allocated DWORD based on an immediate or register value. Eg:
1. d.x86_opcode is one of (OP_ADD, OP_ADC, OP_AND, OP_MOV, OP_OR, OP_SBB, OP_SUB, OP_XOR), i.e.:
2. the dest argument is a mem region:
3. the access size is a DWORD:
4. the dest argument is in the form [ebx-displacement]:
5. the displacement fits within the local funcion stack:
6. the source argument can be anything (i.e. a register or an immediate value): nothing to check!
Case B is very similar, except the arguments are reversed:
1. The dest argument is a register:
2a. The src arg is either another reg:
2b. Or it is an immediate:
2c. Or it is a stack based DWORD:
Finally, case C... Here we:
1. Check that the op is a jmp:
2. Check that it's got an immediate argument:
3. Then we can "jump" to the next position:
mov [ebp-xx], immedB. Arithmetic or logic operation on a 32bit register based on a stack allocated DWORD or an immediate value. Eg:
add [ebp-xx], register
mov register, [ebp-xx]C. A jump to the next chunk of code.Eg:
sub register, other_register
jmp next_chunkMore in details, for case A we check that:
1. d.x86_opcode is one of (OP_ADD, OP_ADC, OP_AND, OP_MOV, OP_OR, OP_SBB, OP_SUB, OP_XOR), i.e.:
d.x86_opcode == OP_ADD || d.x86_opcode == OP_ADC || d.x86_opcode == OP_AND || d.x86_opcode == OP_MOV || d.x86_opcode == OP_OR || d.x86_opcode == OP_SBB || d.x86_opcode == OP_SUB || d.x86_opcode == OP_XOR
d.arg[0].access_type == ACCESS_MEM
d.arg[0].u.mem.access_size == SIZED
d.arg[0].u.mem.scale_reg == REG_EBP && d.arg[0].u.mem.scale == 1 && d.arg[0].u.mem.add_reg == REG_INVALID
d.arg[0].u.mem.displacement <= -4 && d.arg[0].u.mem.displacement >= -(int32_t)stacksize
6. the source argument can be anything (i.e. a register or an immediate value): nothing to check!
Case B is very similar, except the arguments are reversed:
1. The dest argument is a register:
d.arg[0].access_type == ACCESS_REG
2a. The src arg is either another reg:
d.arg[1].access_type == ACCESS_REG
2b. Or it is an immediate:
d.arg[1].access_type == ACCESS_IMM
2c. Or it is a stack based DWORD:
d.arg[0].access_type == ACCESS_MEM && d.arg[0].u.mem.access_size == SIZED && d.arg[0].u.mem.scale_reg == REG_EBP && d.arg[0].u.mem.scale == 1 && d.arg[0].u.mem.add_reg == REG_INVALID && d.arg[0].u.mem.displacement <= -4 && d.arg[0].u.mem.displacement >= -(int32_t)stacksize
Finally, case C... Here we:
1. Check that the op is a jmp:
d.x86_opcode == OP_JMP
2. Check that it's got an immediate argument:
d.arg[0].access_type == ACCESS_REL
3. Then we can "jump" to the next position:
int32_t rel;
seek(cur-4, SEEK_SET); /* move onto the jmp argument */
read(&rel, sizeof(rel)); /* read it */
rel = le32_to_host(rel); /* make it big endian safe */
cur += rel; /* "jump" to it */
Blog post by Alberto Wu.
Monday, October 17, 2011
ClamAV 0.97.3 has been released!
Just released is version 0.97.3 of ClamAV. The following changes are noted in the ChangeLog distributed with the package:
You can download the newest version of ClamAV by visiting the ClamAV.net website, or at the following download links:
Mon Oct 10 14:41:48 CEST 2011 (tk)* freshclam/manager.c: fix error when compiling without DNS support (bb#3056)Sat Oct 8 12:19:49 EEST 2011 (edwin)* libclamav/pdf.c: flag and dump PDF objects with /Launch (bb #3514)Sat Oct 8 12:10:13 EEST 2011 (edwin)* libclamav/bytecode.c,bytecode_api.c: fix recursion level crash (bb #3706).Tue Aug 2 17:03:33 CEST 2011 (tk)* docs: clarify behavior of --scan-*/Scan* options (bb#3134)Mon Jul 25 16:09:19 EEST 2011 (edwin)* libclamav/bytecode_vm.c: fix opcode 20 error (bb #3100)Thu Sep 15 14:44:11 CEST 2011 (tk)* freshclam: fix pidfile removal (bb#3499)Sun Aug 21 17:05:24 EEST 2011 (edwin)* libclamav/pdf.c: fix incorrect blocking of some encrypted PDF with empty user passwords. (bb #3364)Wed Aug 3 15:41:28 CEST 2011 (tk)* sigtool/sigtool.c: fix calculation of max signature lengthYou can download the newest version of ClamAV by visiting the ClamAV.net website, or at the following download links:
Tuesday, October 11, 2011
ClamXav and ClamAV for OSX Lion 10.7
Christoph Murauer, one of the many ClamAV and Snort users in the community has written Snort User guides for Lion which we've linked to before over on the Snort blog.
This time Christoph has written a guide for using ClamXav and ClamAV on OSX Lion 10.7. If you are interested in Antivirus protection for on OSX in any way, I suggest a read of his guide.
Check out the article here.
Thursday, August 25, 2011
Another day, another Rogue Antivirus
Today I have the following on my desk:

The malware usually enters your PC via a drive-by download or the user is tricked into loading the file – for example, if the user wants to see some video on the web and the page tells them that they need an additional plugin. Your Windows security center pops up and tells you that you have no antivirus, no firewall, then the "Antivirus" pops up and starts a scan – it doesn't really scan anything, but shows you a nice animation and claims to detect all kind of malicious software on you disk. If you try to start a program – no matter what, you get the information, that a virus was found and blocked – as a result, you can't run any program – but guess what, help is near and if you purchase the full version of this Antivirus it will help and protect you. Nice of them, isn't it?


In our special case the executable copies itself into the
The removal is quite easy, locate the process in the taskmanager, terminate it, run regedit, terminate the process again (yep, it started again when you started regedit), search the registry for all occurrences of the "three letter" process name. (But make sure that you enter the full path as a search string!) Delete each occurrence and then reboot you machine. After reboot you can also delete the malware executable itself. Done.
Ok, that's really nothing new – but why does it work – as we know a lot of people really click the “Buy now” button and enter their CC information – otherwise such rogue programs wouldn't be so widespread. If you want to see more data on how successful this business is, take a look at the pdf from Alain Zidouemba - it can be found here.
The problem is, that people like you and me – people that work in the computer security field –have no problem to tell the good from the bad, we know all the vendors, we know how to recognize a legit website from a fake, simply because we do this for a living or as a hobby. But what to tell the people that are targeted by such rogue software and that don't have the time, the knowledge and interest in diving into the matter and find out what AV to use and how to tell that it's a real AV and not a fraud? All they want is just “some” AV, or some firewall or whatever.
You can start to tell about various well known vendors, throw with feature lists, ssl certificates, safe browsing and much more and in the end you have someone in front of you, that is bored, confused and / or sleeping.
If you really want to give a short answer, how to make sure that a security product is really a security product and not some fraud – here it is:
The not so short answer – go into a real shop, with real salesman and ask for an antivirus. Whatever you take home with you wont be a rogue antivirus – cause they are only sold on the web but none of them has ever been seen in a computer store, inside a box with a price label on it. Really.
But now, that you read this, – you can also try Immunet Protect – it's not available in stores but works really great – and is combined with ClamAV!

The malware usually enters your PC via a drive-by download or the user is tricked into loading the file – for example, if the user wants to see some video on the web and the page tells them that they need an additional plugin. Your Windows security center pops up and tells you that you have no antivirus, no firewall, then the "Antivirus" pops up and starts a scan – it doesn't really scan anything, but shows you a nice animation and claims to detect all kind of malicious software on you disk. If you try to start a program – no matter what, you get the information, that a virus was found and blocked – as a result, you can't run any program – but guess what, help is near and if you purchase the full version of this Antivirus it will help and protect you. Nice of them, isn't it?


In our special case the executable copies itself into the
%USERPROFILE%\Local Settings\Application Data (for example: C:\Documents and Settings\username\Local Settings\Application Data) with a random, three letter name – like dpx.exe. It also adds some keys to the registry to make sure it will be started upon boot and it also adds a key that makes sure that it will be started as soon as you start a program on you Computer. So much for the self defense.The removal is quite easy, locate the process in the taskmanager, terminate it, run regedit, terminate the process again (yep, it started again when you started regedit), search the registry for all occurrences of the "three letter" process name. (But make sure that you enter the full path as a search string!) Delete each occurrence and then reboot you machine. After reboot you can also delete the malware executable itself. Done.
Ok, that's really nothing new – but why does it work – as we know a lot of people really click the “Buy now” button and enter their CC information – otherwise such rogue programs wouldn't be so widespread. If you want to see more data on how successful this business is, take a look at the pdf from Alain Zidouemba - it can be found here.
The problem is, that people like you and me – people that work in the computer security field –have no problem to tell the good from the bad, we know all the vendors, we know how to recognize a legit website from a fake, simply because we do this for a living or as a hobby. But what to tell the people that are targeted by such rogue software and that don't have the time, the knowledge and interest in diving into the matter and find out what AV to use and how to tell that it's a real AV and not a fraud? All they want is just “some” AV, or some firewall or whatever.
You can start to tell about various well known vendors, throw with feature lists, ssl certificates, safe browsing and much more and in the end you have someone in front of you, that is bored, confused and / or sleeping.
If you really want to give a short answer, how to make sure that a security product is really a security product and not some fraud – here it is:
Buy a box.
The not so short answer – go into a real shop, with real salesman and ask for an antivirus. Whatever you take home with you wont be a rogue antivirus – cause they are only sold on the web but none of them has ever been seen in a computer store, inside a box with a price label on it. Really.
But now, that you read this, – you can also try Immunet Protect – it's not available in stores but works really great – and is combined with ClamAV!
Tuesday, August 9, 2011
70 Percent Of Infected Consumer Machines Hit With Multiple Malware Types
An interesting article over on DarkReading highlighting one of the presentations Sourcefire gave at BlackHat 2011 last week in Las Vegas, NV by our Malware group.
http://www.darkreading.com/cloud-security/167901092/security/antivirus/231300516/70-percent-of-infected-consumer-machines-hit-with-multiple-malware-types.html
http://www.darkreading.com/cloud-security/167901092/security/antivirus/231300516/70-percent-of-infected-consumer-machines-hit-with-multiple-malware-types.html
"Overall, one out of every six or seven consumer machines is infected, according to new malware statistics gathered from Sourcefire's software-based ClamAV and cloud-based Immunet customers during the first three weeks of July."Head on over to the above link for the full article.
Monday, July 25, 2011
ClamAV 0.97.2 is now available
ClamAV 0.97.2 fixes problems with the bytecode engine, Safebrowsing
detection, hash matcher, and other minor issues. Please see
the ChangeLog file for details.
Download : http://downloads.sourceforge.net/clamav/clamav-0.97.2.tar.gz
PGP sig : http://downloads.sourceforge.net/clamav/clamav-0.97.2.tar.gz.sig
Bugfixes : http://www.clamav.net/release-info/bugs/0.97.2
ChangeLog: http://www.clamav.net/release-info/changelog/0.97.2
*** Announcement ***
The ClamAV project is launching a new service called "Third Party web interface". It will allow selected individuals/organizations to publish ClamAV Virus Databases (CVD) through the ClamAV mirror network.
If you choose to publish your signatures through our Third Party web interface you will benefit from the following:
The service is still in beta, you are welcome to contact Luca Gibelli
if you intend to join the beta program.
We especially welcome those who already distribute their own unofficial signatures to join. A list of databases distributed by the new service will be available at http://www.clamav.net/download/cvd/3rdparty
We will be happy to answer any questions you might have.
detection, hash matcher, and other minor issues. Please see
the ChangeLog file for details.
Download : http://downloads.sourceforge.net/clamav/clamav-0.97.2.tar.gz
PGP sig : http://downloads.sourceforge.net/clamav/clamav-0.97.2.tar.gz.sig
Bugfixes : http://www.clamav.net/release-info/bugs/0.97.2
ChangeLog: http://www.clamav.net/release-info/changelog/0.97.2
*** Announcement ***
The ClamAV project is launching a new service called "Third Party web interface". It will allow selected individuals/organizations to publish ClamAV Virus Databases (CVD) through the ClamAV mirror network.
If you choose to publish your signatures through our Third Party web interface you will benefit from the following:
- before publishing the signatures, we will test them for false positives against our false positive file collection.
- before publishing the signatures, we'll verify that the latest two major versions of ClamAV can load them correctly.
- the signatures will be digitally signed and packaged into a single .cvd compressed file.
- there will be no ".UNOFFICIAL" suffix in the detection names.
- a custom prefix will be added to the detection names, identifying the organization which published the signature.
- updates will be distributed both as full CVD files and cdiff incremental updates. Users will benefit from lower network traffic.
- the .cvd and .cdiff files will be distributed through the ClamAV mirror network.
- the service should result in faster remediation of false positives.
- ClamAV users will be able to download the third party databases using freshclam, by adding a single line to freshclam.conf, what should make signature maintenance significantly easier.
The service is still in beta, you are welcome to contact Luca Gibelli
We especially welcome those who already distribute their own unofficial signatures to join. A list of databases distributed by the new service will be available at http://www.clamav.net/download/cvd/3rdparty
We will be happy to answer any questions you might have.
Monday, July 18, 2011
Just for the records
----------- SCAN SUMMARY -----------
Known viruses: 1000066
Engine version: 0.97.1
Scanned directories: 0
Scanned files: 1
Infected files: 1
Known viruses: 1000066
Engine version: 0.97.1
Scanned directories: 0
Scanned files: 1
Infected files: 1
So much work done by so many people - I thought that's worth a post. :-)
Saturday, June 11, 2011
ClamAV 0.97.1 is now available
Recently the ClamAV team here at Sourcefire released version 0.97.1 of the software. You can grab it here. Please see the below pasted changelog for ClamAV since the last version:
Thu Jun 9 08:22:31 CEST 2011 (acab)------------------------------------* libclamav/mew.c: harden boundary check on e8/e9 fixup
Thu May 26 14:17:52 CEST 2011 (acab)------------------------------------* libclamav/matcher-hash.c: in hm_sort don't swap an item with itself (bb#2818)
Thu May 12 13:01:56 CEST 2011 (tk)----------------------------------* freshclam/manager.c: fix return code of Rfc2822DateTime() (bb#2809)
Sat May 7 18:05:23 EEST 2011 (edwin)-------------------------------------* libclamav/pdf.c: better detection for encrypted PDFs (bb #2448)
Fri May 6 16:16:00 EEST 2011 (edwin)------------------------------------* libclamav/c++: add support for building with external LLVM 2.9, and drop external 2.8 support
Thu May 5 01:07:57 CEST 2011 (acab)------------------------------------* clamd: log request ip address for instream scans #bb2592
Wed May 4 14:07:12 EEST 2011 (edwin)-------------------------------------* libclamav/c++/llvm/lib/Target/X86/X86InstrInfo.td: bb #2763don't assert on AVX chips (Intel Core i5 and i7)
Tue May 3 22:52:04 PDT 2011 (tk)---------------------------------* sigtool: properly normalize html files (bb#2764)
Tue May 3 16:14:27 PDT 2011 (tk)---------------------------------* sigtool/sigtool.c: fix formatting of hash dbs (bb#2765)
Wed Apr 27 15:07:22 CEST 2011 (tk)----------------------------------* freshclam: add mirror statistics mechanism
Sat Apr 9 17:20:35 CEST 2011 (acab)------------------------------------* libclamav/pe_icons.c: don't sigbus on sparc (bb#2695)
Sat Apr 9 03:56:17 CEST 2011 (acab)------------------------------------* libclamav/pe.c: reset corrupted status before bytecode hooks (bb#2544)
Thu Mar 17 17:46:09 CET 2011 (tk)---------------------------------* sigtool, freshclam: put .info on top of container to speed up loading
Wed Mar 16 15:53:42 CET 2011 (tk)---------------------------------* sigtool: fix --verify-cdiff
Tue Mar 15 17:56:59 CET 2011 (tk)---------------------------------* sigtool: allow arbitrary names for --build
Wed Mar 9 15:42:50 CET 2011 (tk)---------------------------------* clamdscan: fix file exclusion (bb#2579)
Mon Feb 28 21:46:50 CET 2011 (tk)---------------------------------* clamd: add new option ClamukoExcludeUID (bb#2260)Based on idea from alfred*bokxing.nl
Fri Feb 25 14:49:04 CET 2011 (tk)---------------------------------* libclamav/elf.c: fix incorrect detection of Broken.Executable (bb#2580)
Thu Feb 24 14:52:18 CET 2011 (tk)---------------------------------* shared/output.c: fix empty lines in syslog (bb#2578)
Mon Feb 21 18:19:18 CET 2011 (tk)---------------------------------* clamd: update description of ReadTimeout (bb#2565)
Thu Feb 17 19:13:15 CET 2011 (tk)---------------------------------* clamd: add new config option BytecodeUnsigned (bb#2537); drop"None" from BytecodeSecurity* clamscan: add new switch --bytecode-unsigned and drop --bytecode-trust-all
Tue Feb 15 19:19:31 CET 2011 (tk)---------------------------------* sigtool/sigtool.c: improve handling of bytecode.info (bb#2292)
Thu Apr 14 21:29:36 EEST 2011 (edwin)-------------------------------------* libclamav/others.c: make sure TLS key is initializer (bb #2588).Thanks to Cameron Brown for the detailed analysis of the bug.
Thu Apr 14 13:19:38 EEST 2011 (edwin)-------------------------------------* configure: check for enable_extended_FILE_stdio (bb #2542)
Fri Feb 11 13:16:41 CET 2011 (tk)---------------------------------* sigtool/sigtool.c: handle all signature formats with --(list|find)-sigs (bb#2534)
Tue Feb 8 02:42:11 CET 2011 (acab)-----------------------------------* libclamav/mpoo.c: Make solaris linker happy - Thanks to John Kendall <john*capps.com>
Tuesday, May 10, 2011
MacDefender Blog Post
Wanted to let the readers of this blog know that the VRT has published a blog post concerning the MacDefender OSX Malware over on its blog.
Please check out the post: MacDefender and its variants here.
Please check out the post: MacDefender and its variants here.
Friday, April 1, 2011
2011 Snort Scholarship is now open!
Annually, Sourcefire provides a Snort Scholarship to two individuals selected at random (by drawing) in the amount of $5000 US for higher education purposes.
To be eligible, you must meet the legal criteria found here on our website, sign up for the scholarship here, and following that, on or about May 16, 2011, two winners will be selected.
For further information, please see the links above, also found linked here.
To be eligible, you must meet the legal criteria found here on our website, sign up for the scholarship here, and following that, on or about May 16, 2011, two winners will be selected.
For further information, please see the links above, also found linked here.
Friday, March 25, 2011
How To Integrate ClamAV Into PureFTPd For Virus Scanning On OpenSUSE 11.3
Here's an interesting article on integrating ClamAV with PureFTPD on OpenSUSE. From the article:
How To Integrate ClamAV Into PureFTPd For Virus Scanning On OpenSUSE 11.3 | HowtoForge - Linux Howtos and Tutorials
This tutorial explains how you can integrate ClamAV into PureFTPd for virus scanning on an OpenSUSE 11.3 system. In the end, whenever a file gets uploaded through PureFTPd, ClamAV will check the file and delete it if it is malware.Interesting use of ClamAV to automatically clean the "bad" files from your FTP server upon upload.
I do not issue any guarantee that this will work for you!
How To Integrate ClamAV Into PureFTPd For Virus Scanning On OpenSUSE 11.3 | HowtoForge - Linux Howtos and Tutorials
Monday, March 21, 2011
Top 5 Misconceptions about ClamAV
Millions of people manage ClamAV installations everyday, and the millions of users protected by those installations reap the benefits of its protection engines as their first line of defense against malware threats. ClamAV is deployed inside numerous global ISPs, national telcos, hosting providers, and is utilized by numerous AV gateway vendors like Barracuda and OS vendors like Apple. Without specifically counting all the installations, it’s a pretty easy guess that ClamAV probably has the largest email AV presence in the entire world. I’d even go as far as saying it’s the de-facto standard in gateway AV technology. The main reason for this, based on feedback, is that ClamAV is easy to deploy, works with just about all the MTAs (Sendmail, PostFix, etc), provides pretty darn good protection, is easy to customize, and it’s cheap, heck it’s free.
Whenever I talk to people about ClamAV I always hear the same thing - great mail gateway AV, easy to setup, easy to customize, and it just works. I also always hear the same misconceptions. I think the price of being an ubiquitous technology is people think you do one thing, do that thing really well, and whatever that thing is, you still do it the same way and never evolve. This always leads me to long conversations about things people just don’t know about ClamAV - its engine, the technology, and the people who build it.
Whenever I talk to people about ClamAV I always hear the same thing - great mail gateway AV, easy to setup, easy to customize, and it just works. I also always hear the same misconceptions. I think the price of being an ubiquitous technology is people think you do one thing, do that thing really well, and whatever that thing is, you still do it the same way and never evolve. This always leads me to long conversations about things people just don’t know about ClamAV - its engine, the technology, and the people who build it.
The Top 5 Misconceptions about ClamAV:
- It’s only a Mail Gateway Scanner.
ClamAV is actually a framework. At the core of that framework is what we call libClamAV, this is where all the actual detection happens. This library can be used anywhere that can link to it, so if any application wants to use the power of ClamAV and its detection capabilities the application just needs to link against it. The rest of the framework is all the supporting applications that ClamAV comes with for connecting and running ClamAV in different settings. For instance the ClamD service allows for fast full system and single file scans, clamscan allows for simple on-demand scans, ClamAV-Milter allows for simple integration with MTAs, and freshclam handles keeping everything up to date.
This framework concept makes plugging ClamAV’s detection capabilities into any application really easy and is one of the main reasons ClamAV is used everywhere.
- It’s just a bunch of Open Source hippies writing code in their spare time.
Sourcefire acquired ClamAV in 2007, and retained the entire ClamAV team, eventually the ClamAV team became part of the VRT. These guys are top notch, and do one hell of a job banging out code for ClamAV. The ClamAV feature set has not remained static. On the contrary, in 2010 alone these guys cranked out 6 feature-packed releases, adding tons of new detection features, optimizations, and signature language improvements. On the release front, to put it in context, commercial AV products in the enterprise space get released once every 1 - 2 years.
On top of that we crank though 100s of thousands of new malware samples every day with our automated sandboxes and malware evaluation systems. If you think ClamAV is just an Open Source project, without the same type of systems, data feeds, and technologies in the back office that other AV vendors have, you’d be grossly underestimating our capabilities.
Additionally, the VRT is well known for kicking ass, taking names, and chewing bubble gum in 3rd party validation tests like NSS (where we have consistently come out on top). This industry excellence isn’t limited to Sourcefire’s IPS.
- ClamAV only has a simple content based signature language.
The ClamAV detection engine is multi faceted - heuristics, support for numerous archivers (Zip,Rar,OLE,etc,etc), tons of unpacking support (UPX, PeTite, NSPack, etc), and several different content inspection engines. These content inspection engines range from the simplistic (basic hashing signatures), to the extremely complex (ByteCode engine). In the middle are numerous content matching signature types that support everything you would expect from wildcards, character sets, Boolean logic, and negation. Support for PDF files, Javascript, and HTML files is also included in the engine, along with Mach-O binary support for all the shinny Apple devices out there. With all that support the ClamAV detection engine has everything necessary to detect today’s malware threats, exploits, adware, Trojans, spyware, keyloggers, and much more.
Sometimes detecting those threats requires some real heavy lifting. If that’s the case, the ByteCode engine allows a signature writer to do just about anything they can imagine. Need to implement a quick unpacker for that new piece of malware? Easy. Need to implement a new archiver to unpack something unique? Trivial. Have to do something complex with PDF files? No problem.
The other great thing about ClamAV is that the signature language is open, easy to use, and anyone can add new signatures to their ClamAV installs. If you’ve got something you need to do, and you need to do it now, cause your boss told you to, or the world is ending, it’s pretty darn simple to write your own signatures and add them to your setup.
Also we’ve got some pretty aggressive new features heading out for 0.98 later this year. More on those in the next blog post.
- ClamAV only runs on Unix.
ClamAV has traditionally supported just about every Unix variant on the planet, but as a fully integrated engine in Immunet Protect 3.0 (http://www.immunet.com/), we’ve moved to officially supporting Windows. If you’d like to learn a bit more about Immunet and ClamAV on Windows check out the other posts on the ClamAV blog here.
Immunet Protect adds some additional detection capabilities on Windows platforms including but not limited to:
- Real-Time cloud based protections - No need to download AV updates when running Cloud only protection mode.
- Advanced Machine-Learning detection capabilities.
- Community based protections - Share protection with other members of your Immunet community.
- Real-Time cloud based protections - No need to download AV updates when running Cloud only protection mode.
- ClamAV just can’t be as good as a commercial AV engine, it’s Open Source.
This perception doesn’t surprise me anymore, it’s something we’ve had to deal with since the early days of Snort. There are still a lot people out there that truly believe if it’s a commercial product it’s better than an Open Source product. Normally, this is where the Open Source guys trot out the hundreds of examples of solid Open Source software that have proven they are as good, or better, than commercial offerings. Let's just start with DNS, just about every look up for any Internet request, such as a website, starts out with a DNS query, and those DNS queries are predominately answered by BIND, a solid Open Source Nameserver. Then it’s pretty easy to say MySQL or PostgreSQL run a large portion of your favorite Internet destinations. This list could probably go on for hundreds of paragraphs, just naming all the really excellent Open Source tools that compete for market share with commercial offerings every day.
At the end of the day, though, it’s really not about market share. When you try and compare commercial and Open Source solutions, it’s about effectiveness in solving the problem you, the end user, have. To draw a corollary with Snort, it’s all about detection of the latest network threats. If Snort doesn’t do this correctly, it definitely won’t solve the problem people are expecting it to solve. The only real way to get a handle around this is third-party testing and evaluation, and Snort has done exceptionally well in this area, earning honors for best overall detection at NSS two years running, and certified by ICSALabs in their IPS testing methodology.
When it comes to third-party evaluation of ClamAV, there are a couple of tests to look at. MRG did a third-party evaluation of Immunet Protect (uses ClamAV as one of its engines) where it outscored 15 other leading AV vendors and was the ONLY product that had a 100% detection rate. Additionally, ShadowServer does daily evaluations of numerous AV technologies; while ClamAV doesn’t come in number one, we do beat out numerous commercial AVs on a daily and yearly basis. Here are the stats for the last year: http://www.shadowserver.org/wiki/pmwiki.php/Stats/VirusYearlyStats.
Wednesday, March 16, 2011
59 Open Source Tools that Can Replace Popular Security Software
This article over at Datamation talks about 59 Open Source Tools that can Replace Popular Security Software.
It talks about ClamAV in two instances, saying that ClamAV is a replacement for antivirus software, referencing Immunet. Then it mentions ClamAVWin for Windows. ClamAV for the Windows OS is now officially rolled up into Immunet 3.0 - powered by ClamAV. So while Datamation gives ClamAV two plugs, for the Windows platform, we are calling it Immunet, for Unix based platforms, ClamAV retains the same name.
While there is no mention of Snort in the article, funnily enough, many other products that are in the article incorporate Snort. So we're sure it's just an oversight. There are a lot of OpenSource tools out there, support your communities, support OpenSource, and use the tools. Provide code, feedback, and information. Help us all make the tools easier to use and loads more powerful.
It talks about ClamAV in two instances, saying that ClamAV is a replacement for antivirus software, referencing Immunet. Then it mentions ClamAVWin for Windows. ClamAV for the Windows OS is now officially rolled up into Immunet 3.0 - powered by ClamAV. So while Datamation gives ClamAV two plugs, for the Windows platform, we are calling it Immunet, for Unix based platforms, ClamAV retains the same name.
While there is no mention of Snort in the article, funnily enough, many other products that are in the article incorporate Snort. So we're sure it's just an oversight. There are a lot of OpenSource tools out there, support your communities, support OpenSource, and use the tools. Provide code, feedback, and information. Help us all make the tools easier to use and loads more powerful.
Monday, February 21, 2011
Realtime protection with ClamAV on Windows
One of the major features in Immunet 3.0 powered by ClamAV is the integration of the full ClamAV engine for "offline protection, advanced archive and unpacking support, and custom signature creation". What does that mean though?
First of all it means that when you are not connected to the cloud then you are protected by the locally installed ClamAV engine. What may not be clear from that feature description is that ClamAV is also used when you are online, and it is used for realtime protection (on-access scanning) too!
Is the ClamAV engine enabled by default in Immunet 3.0?
That depends on how you install it, but you can always change the settings later. In fact it is easy to test if the local ClamAV engine is enabled and working, as I'll show you next:
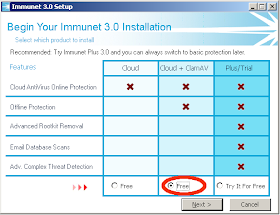
Download the Immunet 3.0 powered by ClamAV installer from here, and run it.
Make sure you select Cloud + ClamAV as shown here, and then proceed with the installation:
Once installed you can check whether ClamAV is enabled (and enable if not):
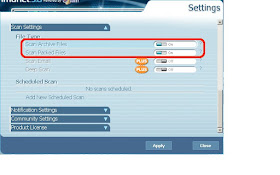
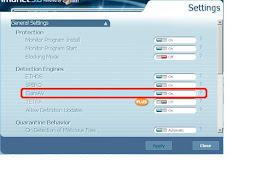 Then check that archive and packed file scanning is enabled:
Then check that archive and packed file scanning is enabled:
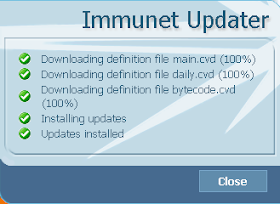
 Finally click on "Update Now" to make sure your antivirus database is up-to-date:
Finally click on "Update Now" to make sure your antivirus database is up-to-date:
To test the local ClamAV engine you can use the following test file, (which is completely safe, it is not even executable):
Open notepad, then Copy and Paste this text exactly as shown here:
$CEliacmaTrESTuScikgsn$FREE-TEST-SIGNATURE$EEEEE$
Once you save the file (lets call it clam.txt for example) you should get a popup from Immunet showing that it has detected Clam.ClamAV-Test-Signature:
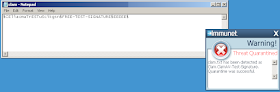 You can open the folder you tried to save the file in, and check that it is really gone.
You can open the folder you tried to save the file in, and check that it is really gone.
Now you should be confident that you are protected by ClamAV's engine in "Immunet 3.0 powered by ClamAV".
How do you know which engine detected the file?
works together with the cloud read on.
A scan can be triggered by:
If a malware is detected the file is quarantined, and the malicious process is blocked, prevented from execution.
So you see when you have both the cloud and ClamAV enabled it performs a more thorough scan than when scanning with both individually.
What if a file is detected by both the cloud and the local ClamAV engine?
Currently the detection from the cloud wins, but that may change as we work on optimizing the integration of the engine. Also just because you see a cloud detection, it doesn't mean the local engine wouldn't have detected it.
First of all it means that when you are not connected to the cloud then you are protected by the locally installed ClamAV engine. What may not be clear from that feature description is that ClamAV is also used when you are online, and it is used for realtime protection (on-access scanning) too!
Is the ClamAV engine enabled by default in Immunet 3.0?
That depends on how you install it, but you can always change the settings later. In fact it is easy to test if the local ClamAV engine is enabled and working, as I'll show you next:
Download the Immunet 3.0 powered by ClamAV installer from here, and run it.
Make sure you select Cloud + ClamAV as shown here, and then proceed with the installation:

Once installed you can check whether ClamAV is enabled (and enable if not):
 Then check that archive and packed file scanning is enabled:
Then check that archive and packed file scanning is enabled: Finally click on "Update Now" to make sure your antivirus database is up-to-date:
Finally click on "Update Now" to make sure your antivirus database is up-to-date:
To test the local ClamAV engine you can use the following test file, (which is completely safe, it is not even executable):
Open notepad, then Copy and Paste this text exactly as shown here:
$CEliacmaTrESTuScikgsn$FREE-TEST-SIGNATURE$EEEEE$
Once you save the file (lets call it clam.txt for example) you should get a popup from Immunet showing that it has detected Clam.ClamAV-Test-Signature:
 You can open the folder you tried to save the file in, and check that it is really gone.
You can open the folder you tried to save the file in, and check that it is really gone.Now you should be confident that you are protected by ClamAV's engine in "Immunet 3.0 powered by ClamAV".
How do you know which engine detected the file?
- if the virusname starts with "W32." then it is a cloud detection
- if it starts with "W32.SPERO.", it is a cloud detection from the SPERO heuristic engin
- if it starts with "W32.ETHOS.", it is a cloud detection from the ETHOS heuristic engine
- if it starts with "W32.Clam.", it is a file that was detected by ClamAV on the cloud
- if it starts with "Clam.", it is a local ClamAV detection
- if it starts with "Clam." and ends with ".UNOFFICIAL", then it is your custom signature
works together with the cloud read on.
A scan can be triggered by:
- on-access, i.e. realtime protection: when you launch an application, copy or move files
- on-demand, via the "Scan Now" button
- scheduled scan, which can be configured in "Scan Settings", "Add New Scheduled Scan
- scans the file using the cloud (by sending the file's fingerprints), if you are online
- if the ClamAV engine is enabled it starts scanning the file, as usual:
- using its (official or custom) signatures database
- scanning files inside archives (if enabled in Settings)
- scanning inside packed executables (if enabled in Settings)
- each of these inner files (inside archives, packed executables) is
- scanned using the cloud as well
- ClamAV checks its local whitelist when it detects a virus
- as soon as either engine finds a malware, scanning is stopped
- the cloud also checks its whitelist for both its own detections and ClamAV's detections
If a malware is detected the file is quarantined, and the malicious process is blocked, prevented from execution.
So you see when you have both the cloud and ClamAV enabled it performs a more thorough scan than when scanning with both individually.
What if a file is detected by both the cloud and the local ClamAV engine?
Currently the detection from the cloud wins, but that may change as we work on optimizing the integration of the engine. Also just because you see a cloud detection, it doesn't mean the local engine wouldn't have detected it.
Friday, February 11, 2011
How to create custom signatures for Immunet 3.0, powered by ClamAV
Immunet 3.0 is Sourcefire’s new cloud-based desktop anti-malware solution for Microsoft Windows. For best performance, an Internet connection is recommended. Additionally, Immunet 3.0 is powered by ClamAV, which allows users to stay protected even when not connected to the Immunet cloud. ClamAV built its reputation over the years on the UNIX platform as being a robust and capable enterprise-level anti-malware solution, which allows the advanced user to create their own signatures to complement the ones supplied and updated several times a day by Sourcefire.
Why is being able to use your custom signatures a great feature? Well, it’s because you can make your anti-malware program look for threats that you are the first to see or that you will be the only one to see (e.g. Advanced Persistent Threats, or APT). Or, you could have found that an older version of a proprietary program that's running on your network is vulnerable and you want to make sure that users only run the latest version. Writing a custom signature that targets the older program, can help you enforce that policy.
Here's how to get started on writing your own custom ClamAV signatures for Immunet 3.0.
Download the ClamAV command-line Signature Tool, sigtool (MD5:838f6b4ea87199b86f04e9efb96241c3). Now let’s say that test.exe is the file you want to create a signature for. To create a signature that will match only that file, use the --md5 option of sigtool (in this example, I am redirecting the output from sigtool into a file with a .hdb extension):

Pic.1: Signature using full MD5 hash of file.
Now, in this case the signature will match on only one file. You may want to write something that matches on multitple files. For example, in the case of executable files you may want to write a signature that will match a particular PE-section, and all files that have the same PE-section. To do so, break up your executable into its different PE-sections either manually or by using tools, identify the one you want to write a signature for (typically the sections are labelled .text, .rdata, .data, .idata, etc..) and use the --mdb option of sigtool (in this example I am redirecting the output from sigtool into a file with a .mdb extension):

Pic.2: Signature using the hash of the PE-section of an executable.
Another way to have ClamAV detect a file is to base your signature on a hexadecimal fragment contained within the body of the file. Let's say you have a text file that contains the text I look like a benign file but actually I am a bad script and I will pwn your machine, if you don't pay attention. We decide that our detection will be based on detecting the phrase I am a bad script in any text files. To write a signature, we can start by echoing I am a bad script into sigtool --hex-dump (this time I'm not redirecting output into a file just yet):

Pic.3: Signature using the a hex fragment of a file.
Then I'm going to create a signature that has the format Name:TargetType:Offset:HexSignature and redirect it to a file with a .ndb extension, like I did at the end of the example above. You'll notice that I did not include the line break 0d0a in the hex signature.
For more in-depth information on how to create signatures, check out the documentation on Creating Signatures for ClamAV. There is also a webcast on the topic as well as a blog entry on how to create logical signatures for ClamAV.
Well, all that is good and I've created signatures, how do I load them into Immunet 3.0? You may very well ask.
First things first: Make sure that the ClamAV detection engine is turned on. Open Immunet 3.0, select “Settings” and switch the ClamAV “on”. Click on “Apply”.

Pic.4: Making sure that the ClamAV engine is turned on.
Optional (but highly recommended): Back in the main pane, click on “Update Now” to download the latest official ClamAV signatures.

Pic.5: "Update Now" to get the latest official ClamAV signatures.
Next, launch SigUI from Start->All Programs->Immunet 3.0->Custom Signature Tool.

Pic.6: SigUI's interface.
SigUI is a graphical user interface used to configure a back-end tool called Freshclam, which is used to download ClamAV signatures. Under the "Updater configuration”tab, you can enter proxy settings if you access the Internet using a proxy. To ensure that the settings have been entered properly, click on "Run freshclam to test configuration". Upon successfully accessing the Internet, Freshclam will exit without error (“Freshclam exited with code: 0”) (see Pic. 7):

Pic.7: Freshclam running.
Next, from the pull-down menu "Download Official Signatures from mirror", select where you want to download official ClamAV signatures from. By default, official signatures will be fetched from db.local.clamav.net. Although this works well most of the time, you may get better performance by using a server closer to your location. Mirrors are in the form db.XY.clamav.net, where XY is a two-letter country code. Alternatively, you can manually enter a hostname, such as your own server if that is where you are hosting the official ClamAV signatures. This completes the configuration for the automatic retrieval of official signatures.
To deploy your own signatures (or signatures provided by third-parties), you can either:
- specify their full URI (URL or UNC path) under Custom signatures URLs (see Pic. 6). The signatures can be in any format that ClamAV understands
- add the signatures file(s) under the "Local signature management tab" (see Pic. 8). At that point the signature aren’t yet installed. You must click on Verify and Install signatures to test the new signatures (see Pic. 9). The ones that pass verification will be installed and ClamAV will load them at the next database update

Pic.8: SigUI's "Local signature management" tab

Pic.9: Signatures installed after verification
Your custom signatures will be copied to the ClamAV signatures folder and loaded the next time the system is idle.
Voila! You now know how to write and deploy your own ClamAV signatures. You can also load third-party signatures written in the a format that ClamAV understands the same way you would your custom signatures. Again, you don't have to write your own signatures, but you can if you want and that is a powerful feature at your disposal. Feel free to contribute your signatures to our online forum. Feel free to post your questions to our mailing list. Additionally, you will find someone to answer your questions in the IRC chat room #clamav on irc.freenode.net.
Why is being able to use your custom signatures a great feature? Well, it’s because you can make your anti-malware program look for threats that you are the first to see or that you will be the only one to see (e.g. Advanced Persistent Threats, or APT). Or, you could have found that an older version of a proprietary program that's running on your network is vulnerable and you want to make sure that users only run the latest version. Writing a custom signature that targets the older program, can help you enforce that policy.
Here's how to get started on writing your own custom ClamAV signatures for Immunet 3.0.
Download the ClamAV command-line Signature Tool, sigtool (MD5:838f6b4ea87199b86f04e9efb96241c3). Now let’s say that test.exe is the file you want to create a signature for. To create a signature that will match only that file, use the --md5 option of sigtool (in this example, I am redirecting the output from sigtool into a file with a .hdb extension):
Pic.1: Signature using full MD5 hash of file.
Now, in this case the signature will match on only one file. You may want to write something that matches on multitple files. For example, in the case of executable files you may want to write a signature that will match a particular PE-section, and all files that have the same PE-section. To do so, break up your executable into its different PE-sections either manually or by using tools, identify the one you want to write a signature for (typically the sections are labelled .text, .rdata, .data, .idata, etc..) and use the --mdb option of sigtool (in this example I am redirecting the output from sigtool into a file with a .mdb extension):
Pic.2: Signature using the hash of the PE-section of an executable.
Another way to have ClamAV detect a file is to base your signature on a hexadecimal fragment contained within the body of the file. Let's say you have a text file that contains the text I look like a benign file but actually I am a bad script and I will pwn your machine, if you don't pay attention. We decide that our detection will be based on detecting the phrase I am a bad script in any text files. To write a signature, we can start by echoing I am a bad script into sigtool --hex-dump (this time I'm not redirecting output into a file just yet):
Pic.3: Signature using the a hex fragment of a file.
Then I'm going to create a signature that has the format Name:TargetType:Offset:HexSignature and redirect it to a file with a .ndb extension, like I did at the end of the example above. You'll notice that I did not include the line break 0d0a in the hex signature.
For more in-depth information on how to create signatures, check out the documentation on Creating Signatures for ClamAV. There is also a webcast on the topic as well as a blog entry on how to create logical signatures for ClamAV.
Well, all that is good and I've created signatures, how do I load them into Immunet 3.0? You may very well ask.
First things first: Make sure that the ClamAV detection engine is turned on. Open Immunet 3.0, select “Settings” and switch the ClamAV “on”. Click on “Apply”.
Pic.4: Making sure that the ClamAV engine is turned on.
Optional (but highly recommended): Back in the main pane, click on “Update Now” to download the latest official ClamAV signatures.
Pic.5: "Update Now" to get the latest official ClamAV signatures.
Next, launch SigUI from Start->All Programs->Immunet 3.0->Custom Signature Tool.
Pic.6: SigUI's interface.
SigUI is a graphical user interface used to configure a back-end tool called Freshclam, which is used to download ClamAV signatures. Under the "Updater configuration”tab, you can enter proxy settings if you access the Internet using a proxy. To ensure that the settings have been entered properly, click on "Run freshclam to test configuration". Upon successfully accessing the Internet, Freshclam will exit without error (“Freshclam exited with code: 0”) (see Pic. 7):
Pic.7: Freshclam running.
Next, from the pull-down menu "Download Official Signatures from mirror", select where you want to download official ClamAV signatures from. By default, official signatures will be fetched from db.local.clamav.net. Although this works well most of the time, you may get better performance by using a server closer to your location. Mirrors are in the form db.XY.clamav.net, where XY is a two-letter country code. Alternatively, you can manually enter a hostname, such as your own server if that is where you are hosting the official ClamAV signatures. This completes the configuration for the automatic retrieval of official signatures.
To deploy your own signatures (or signatures provided by third-parties), you can either:
- specify their full URI (URL or UNC path) under Custom signatures URLs (see Pic. 6). The signatures can be in any format that ClamAV understands
- add the signatures file(s) under the "Local signature management tab" (see Pic. 8). At that point the signature aren’t yet installed. You must click on Verify and Install signatures to test the new signatures (see Pic. 9). The ones that pass verification will be installed and ClamAV will load them at the next database update
Pic.8: SigUI's "Local signature management" tab
Pic.9: Signatures installed after verification
Your custom signatures will be copied to the ClamAV signatures folder and loaded the next time the system is idle.
Voila! You now know how to write and deploy your own ClamAV signatures. You can also load third-party signatures written in the a format that ClamAV understands the same way you would your custom signatures. Again, you don't have to write your own signatures, but you can if you want and that is a powerful feature at your disposal. Feel free to contribute your signatures to our online forum. Feel free to post your questions to our mailing list. Additionally, you will find someone to answer your questions in the IRC chat room #clamav on irc.freenode.net.
Wednesday, February 9, 2011
Sourcefire Unveils Immunet 3.0, with Customized Protection Against Zero-Day Threats and Automated Remediation of Infected Files
Columbia, MD – February 09, 2011 -- Sourcefire, Inc. (Nasdaq: FIRE), the creator of Snort® and a leader in intelligent cybersecurity solutions, today announced the availability of Immunet™ 3.0, which leverages a cloud-based collective immunity platform to deliver real-time protection against zero-day attacks. Immunet 3.0 enables businesses and consumers to create custom anti-malware signatures for more accurate protection against targeted attacks and offers an innovative Cloud Recall™ feature, which can remediate previously approved files, automatically quarantining them in real time based on new threat information.
“Immunet 3.0 changes the way anti-malware works. By leveraging the cloud and allowing users to create custom signatures, Sourcefire is increasing the speed and accuracy of its protection to align with the demands of today’s environments,” said Charles Kolodgy, research Vice president at IDC. “With the added ability to protect against malware introduced by non-traditional means, including rootkits and USB drives, Immunet 3.0 is offering customers the functionality they require, while filling significant holes that have been left by more traditional solutions.”
Backed by the additional resources of Sourcefire®, Immunet 3.0 offers significant advancements that enable consumers and businesses to protect their PCs from Client-Side attacks. These include:
“When it comes to protecting against new and targeted threats, traditional anti-malware solutions typically fall short because of the time it takes to push new signatures,” said Martin Roesch, Sourcefire’s CTO and Founder. “Sourcefire’s approach is revolutionizing the way consumers and organizations protect their endpoints. By leveraging our innovative cloud platform and enabling customers to create custom signatures, Immunet 3.0 is offering consumers and businesses the ability to take a more proactive stance with their anti-malware investments and better protect against the latest attacks that traditional solutions miss.”
About Sourcefire
Sourcefire, Inc. (Nasdaq:FIRE), is a world leader in intelligent cybersecurity solutions. Sourcefire is transforming the way Global 2000 organizations and government agencies manage and minimize network security risks. Sourcefire’s IPS, RNA® (Real-time Network Awareness) and Real-time Adaptive Security solutions equip customers with an efficient and effective layered security defense – protecting network assets before, during and after an attack. Through the years, Sourcefire has been consistently recognized for its innovation and industry leadership by customers, media and industry analysts alike – with more than 50 awards and accolades. Today, the name Sourcefire has grown synonymous with innovation and network security intelligence. For more information about Sourcefire, please visit http://www.sourcefire.com.
SOURCEFIRE®, Sourcefire IPS™, SNORT®, RAZORBACK™, the Sourcefire logo, the Snort and Pig logo, SECURITY FOR THE REAL WORLD™, SOURCEFIRE DEFENSE CENTER®, SOURCEFIRE 3D®, RNA®, RUA®, DAEMONLOGGER™, CLAMAV®, IMMUNET™ and certain other trademarks and logos are trademarks or registered trademarks of Sourcefire, Inc. in the United States and other countries. Other company, product and service names may be trademarks or service marks of others.
“Immunet 3.0 changes the way anti-malware works. By leveraging the cloud and allowing users to create custom signatures, Sourcefire is increasing the speed and accuracy of its protection to align with the demands of today’s environments,” said Charles Kolodgy, research Vice president at IDC. “With the added ability to protect against malware introduced by non-traditional means, including rootkits and USB drives, Immunet 3.0 is offering customers the functionality they require, while filling significant holes that have been left by more traditional solutions.”
Backed by the additional resources of Sourcefire®, Immunet 3.0 offers significant advancements that enable consumers and businesses to protect their PCs from Client-Side attacks. These include:
- Custom Signature Creation – While customization is available in some enterprise security solutions, including Intrusion Prevention Systems, traditional antivirus offerings continue to take a “black box” mentality to customization. With Immunet 3.0, customers now have the power to create signatures for their specific requirements, significantly improving the effectiveness of Immunet.
- Cloud Recall – This new, innovative feature leverages the power of the Immunet platform to provide increased endpoint protection. Through continuous file processing in the cloud, Immunet 3.0 can retroactively quarantine a file that was originally cleared, but later deemed to be malware. The Immunet Community is updated automatically as new threats are discovered. Cloud Recall provides a significant advantage over traditional approaches to solving this problem, which include sending 20,000 - 40,000 signatures down to each and every endpoint on a daily basis, then invoking a resource-intensive full system scan.
- Collective Immunity™ – A key benefit of Immunet 3.0 is Collective Immunity, which allows users to harness the collective presence of Immunet’s 850,000 worldwide users for increased endpoint protection. This cloud-based approach enables organizations to better protect against zero-day attacks with real-time protection driven by intelligence from the user community. Each time someone in this collective community encounters a threat, everyone else in the community automatically gains protection from that same threat in real time. Customers no longer have to rely on the isolated security of their traditional antivirus vendor.
“When it comes to protecting against new and targeted threats, traditional anti-malware solutions typically fall short because of the time it takes to push new signatures,” said Martin Roesch, Sourcefire’s CTO and Founder. “Sourcefire’s approach is revolutionizing the way consumers and organizations protect their endpoints. By leveraging our innovative cloud platform and enabling customers to create custom signatures, Immunet 3.0 is offering consumers and businesses the ability to take a more proactive stance with their anti-malware investments and better protect against the latest attacks that traditional solutions miss.”
About Sourcefire
Sourcefire, Inc. (Nasdaq:FIRE), is a world leader in intelligent cybersecurity solutions. Sourcefire is transforming the way Global 2000 organizations and government agencies manage and minimize network security risks. Sourcefire’s IPS, RNA® (Real-time Network Awareness) and Real-time Adaptive Security solutions equip customers with an efficient and effective layered security defense – protecting network assets before, during and after an attack. Through the years, Sourcefire has been consistently recognized for its innovation and industry leadership by customers, media and industry analysts alike – with more than 50 awards and accolades. Today, the name Sourcefire has grown synonymous with innovation and network security intelligence. For more information about Sourcefire, please visit http://www.sourcefire.com.
SOURCEFIRE®, Sourcefire IPS™, SNORT®, RAZORBACK™, the Sourcefire logo, the Snort and Pig logo, SECURITY FOR THE REAL WORLD™, SOURCEFIRE DEFENSE CENTER®, SOURCEFIRE 3D®, RNA®, RUA®, DAEMONLOGGER™, CLAMAV®, IMMUNET™ and certain other trademarks and logos are trademarks or registered trademarks of Sourcefire, Inc. in the United States and other countries. Other company, product and service names may be trademarks or service marks of others.
Tuesday, February 8, 2011
Immunet 3.0 - Powered by ClamAV
Tomorrow, February 9th, will mark the day that the Immunet 3.0 product from Sourcefire officially rolls out. Immunet 3.0, not only has the familiar Immunet cloud based anti-virus product that you are used to, but it also builds in the ClamAV 0.97 engine for even more detection from threats.
We are no longer calling the product "ClamAV for Windows 3.0", we are now referring to the product as "Immunet 3.0".
New Features:
We are no longer calling the product "ClamAV for Windows 3.0", we are now referring to the product as "Immunet 3.0".
New Features:
- Offline Protection -- This is the ClamAV portion, allowing you to stay protected even while not connected to the Immunet cloud.
- Cloud Recall -- Even if the file that Immunet scanned today is "clean", and tomorrow it's discovered the file is bad, Immunet will still get it.
- Custom Signature Generation -- This gives advanced users the ability to create your own anti-virus signatures for new emerging threats. With the Immunet 3.0 release, we are the only Windows based anti-virus product to allow you to do this.
This is a great release, building in a lot of features and combining the power of ClamAV with the power of the cloud of Immunet is quite an achievement.
Check out the blog post from Al Huger over on the Immunet blog for further information. I'll put a formal announcement up tomorrow.
Monday, February 7, 2011
ClamAV 0.97 has been released!
Since the release of ClamAV 0.97rc, there have been several bug fixes:
ClamAV 0.97 brings many improvements, including complete Windows support (all major components compile out-of-box under Visual Studio), support for signatures based on SHA1 and SHA256, better error detection, as well as speed and memory optimizations. The complete list of changes is available in the ChangeLog file. For upgrade notes and tips please see: https://wiki.clamav.net/Main/UpgradeNotes097
Download: http://downloads.sourceforge.net/cla...av-0.97.tar.gz
PGP sig: http://downloads.sourceforge.net/cla....97.tar.gz.sig
Bugfixes: http://www.clamav.net/release-info/bugs/0.97
ChangeLog: http://www.clamav.net/release-info/changelog/0.97
We'll have further information regarding ClamAV this week, stay tuned to the blog to find out more!
* libclamav/vba_extract.c: fix error path double free (bb#2486) * libclamav/phishcheck.c: fix some missed safebrowsing URLs (bb #2514) * libclamav/matcher-bm.c: fix error message (bb#2513) * libclamav/matcher-hash.c: stop leaking virusnames (nopool mode)So anyone using the RC, or a previous version of ClamAV should go ahead and take the opportunity to update to 0.97 now.
ClamAV 0.97 brings many improvements, including complete Windows support (all major components compile out-of-box under Visual Studio), support for signatures based on SHA1 and SHA256, better error detection, as well as speed and memory optimizations. The complete list of changes is available in the ChangeLog file. For upgrade notes and tips please see: https://wiki.clamav.net/Main/UpgradeNotes097
Download: http://downloads.sourceforge.net/cla...av-0.97.tar.gz
PGP sig: http://downloads.sourceforge.net/cla....97.tar.gz.sig
Bugfixes: http://www.clamav.net/release-info/bugs/0.97
ChangeLog: http://www.clamav.net/release-info/changelog/0.97
We'll have further information regarding ClamAV this week, stay tuned to the blog to find out more!
Wednesday, February 2, 2011
ClamAV 0.97rc is available for download
The release candidate for ClamAV 0.97 is available for download.
ClamAV 0.97 brings many improvements, including complete Windows support
(all major components compile out-of-box under Visual Studio), support
for signatures based on SHA1 and SHA256, better error detection, as well as
speed and memory optimizations. The complete list of changes is
available in the ChangeLog file. For upgrade notes and tips please see:
https://wiki.clamav.net/Main/UpgradeNotes097
We encourage as many people as possible to test this release.
If you don't have access to a test machine you can still help
by downloading it and checking for us that it compiles and links
on your platform and by running "make check".
If you do have a test machine/model/network please help us by loading
ClamAV 0.97rc and testing.
All bug reports should be filed at http://bugs.clamav.net.
We also encourage all 3rd party developers of products and
distribution/port maintainers to download and check this update so that
you can go live as soon as the final version is released.
Download : http://downloads.sourceforge.net/clamav/clamav-0.97rc.tar.gz
PGP sig : http://downloads.sourceforge.net/clamav/clamav-0.97rc.tar.gz.sig
Bugfixes : http://www.clamav.net/release-info/bugs/0.97
ChangeLog: http://git.clamav.net/gitweb?p=clamav-devel.git;a=blob_plain;f=ChangeLog;hb=clamav-0.97rc
ClamAV 0.97 brings many improvements, including complete Windows support
(all major components compile out-of-box under Visual Studio), support
for signatures based on SHA1 and SHA256, better error detection, as well as
speed and memory optimizations. The complete list of changes is
available in the ChangeLog file. For upgrade notes and tips please see:
https://wiki.clamav.net/Main/UpgradeNotes097
We encourage as many people as possible to test this release.
If you don't have access to a test machine you can still help
by downloading it and checking for us that it compiles and links
on your platform and by running "make check".
If you do have a test machine/model/network please help us by loading
ClamAV 0.97rc and testing.
All bug reports should be filed at http://bugs.clamav.net.
We also encourage all 3rd party developers of products and
distribution/port maintainers to download and check this update so that
you can go live as soon as the final version is released.
Download : http://downloads.sourceforge.net/clamav/clamav-0.97rc.tar.gz
PGP sig : http://downloads.sourceforge.net/clamav/clamav-0.97rc.tar.gz.sig
Bugfixes : http://www.clamav.net/release-info/bugs/0.97
ChangeLog: http://git.clamav.net/gitweb?p=clamav-devel.git;a=blob_plain;f=ChangeLog;hb=clamav-0.97rc
Monday, January 31, 2011
Malware Research Group tests say Immunet is #1
Check out this test over at the Malware Research Group. The MRG tests most of the top anti-malware software vendors for coverage and features and it turns out as a result of this particular test, that MRG rates that Immunet comes out on top!
Check out the test results here.
Check out the test results here.
Friday, January 21, 2011
PCWorld writes about ClamAV and Immunet
It's great to see the news coming out about our ClamAV 3.0 product for Windows, seems Keir Thomas of PCWorld wrote the article linked below. Here's a couple of choice quotes:
"The key new feature in version 3 is offline scanning. Because of its cloud nature, ClamAV for Windows ideally requires an Internet connection in order to check files against virus definitions, but with version 3 the ClamAV engine and virus definitions are also held locally, so virus scans are possible when the Internet isn't present."
"When I ran the software for testing purposes it told me it protected against just over 19 million threats, and that around 800,000 people were connected to the Immunet Protect cloud alongside me. It's difficult to argue with such figures."
The article states that they don't know when the final release of ClamAV 3.0 for Windows will be released, but we'll tell you that it will be soon, and we'll let you know when it is ready!
ClamAV Promises Free Antivirus App For Businesses
ClamAV Promises Free Antivirus App For Businesses
Thursday, January 20, 2011
Are you speaking about ClamAV?
Are you attending a Security Conference where there is a presentation on ClamAV?
Are you presenting at a Security Conference about ClamAV?
Email me! I'd like to have a running list of Security Conferences with presentations about our OpenSource technologies. We'll maintain it on the website and help publicize the speaking engagement for you!
Thanks!
Are you presenting at a Security Conference about ClamAV?
Email me! I'd like to have a running list of Security Conferences with presentations about our OpenSource technologies. We'll maintain it on the website and help publicize the speaking engagement for you!
Thanks!
Friday, January 7, 2011
ClamAV 3.0 for Windows Open Beta
The public beta for ClamAV 3.0 for Windows, which includes full integration of the ClamAV engine into the Immunet Protect product is now open. If you are interested in playing with ClamAV 3.0 for Windows please check out the following link:
http://forum.immunet.com/index.php?/topic/562-clamav-for-windows-beta-clamlib-integration
The download links are here:
(32 Bit Systems) - http://www.clamav.net/win32/ClamAVWindowsSetup-beta-32.exe
(64 Bit Systems) - http://www.clamav.net/win32/ClamAVWindowsSetup-beta-64.exe
Main feature overview:
Because this is a Beta 1:
Please report bugs at https://wwws.clamav.net/bugzilla. Remember to attach a run of the System Diag Tool to help speed up fixing the problem. (its located in the Program Folder for ClamAV for Windows).
It drops a zip file on the desktop.
Known issues:
1. Binaries are still labeled 2.0
2. Scan history screen contains duplicate entries.
http://forum.immunet.com/index.php?/topic/562-clamav-for-windows-beta-clamlib-integration
The download links are here:
(32 Bit Systems) - http://www.clamav.net/win32/ClamAVWindowsSetup-beta-32.exe
(64 Bit Systems) - http://www.clamav.net/win32/ClamAVWindowsSetup-beta-64.exe
Main feature overview:
- ClamAV 0.96.5 libraries for real-time scanning and offline scanning
- Customizable signatures support and signature creation UI
- Wildcard exclusions - specifically so we can exclude Thunderbird's %TEMP%\nsmail*.tmp
- Unicode bug fixes
- Bug fix for user's getting in a disconnected state
Because this is a Beta 1:
- It is strongly recommended that you test on a VM
- See https://www.clamav.net/bugzilla and
- http://forum.immunet.com/index.php?/topic/562-clamav-for-windows-beta-clamlib-integration for any additional known defects.
- The SigUI - This allows you to create your own ClamAV signatures and load them into the engine. Its both a GUI, and a command line tool. Documentation is available here: http://support.immunet.com/tiki-read_article.php?articleId=24
- Writing ClamAV signatures documentation is here: http://www.clamav.net/doc/latest/signatures.pdf
Please report bugs at https://wwws.clamav.net/bugzilla. Remember to attach a run of the System Diag Tool to help speed up fixing the problem. (its located in the Program Folder for ClamAV for Windows).
It drops a zip file on the desktop.
Known issues:
1. Binaries are still labeled 2.0
2. Scan history screen contains duplicate entries.
The ClamAV Blog is back!
After a hiatus of, wow, almost 2 years, the ClamAV blog is back!
Here we'll post news about our newest releases of ClamAV, news surrounding the project, technical tips, and how you can better use it to protect your computer and network.
If you have any feedback or suggestions of topics you'd like to see written about on the ClamAV blog, don't hesitate to email me!
Thanks for supporting ClamAV! We look forward to a great 2011.
Joel Esler
jesler [at] sourcefire [dot] com
Manager, OpenSource Community
Here we'll post news about our newest releases of ClamAV, news surrounding the project, technical tips, and how you can better use it to protect your computer and network.
If you have any feedback or suggestions of topics you'd like to see written about on the ClamAV blog, don't hesitate to email me!
Thanks for supporting ClamAV! We look forward to a great 2011.
Joel Esler
jesler [at] sourcefire [dot] com
Manager, OpenSource Community
