First of all it means that when you are not connected to the cloud then you are protected by the locally installed ClamAV engine. What may not be clear from that feature description is that ClamAV is also used when you are online, and it is used for realtime protection (on-access scanning) too!
Is the ClamAV engine enabled by default in Immunet 3.0?
That depends on how you install it, but you can always change the settings later. In fact it is easy to test if the local ClamAV engine is enabled and working, as I'll show you next:
Download the Immunet 3.0 powered by ClamAV installer from here, and run it.
Make sure you select Cloud + ClamAV as shown here, and then proceed with the installation:
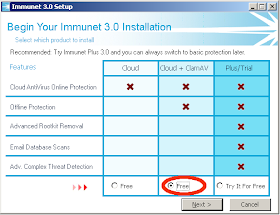
Once installed you can check whether ClamAV is enabled (and enable if not):
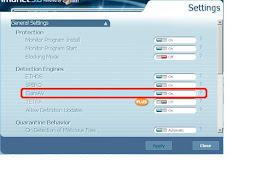 Then check that archive and packed file scanning is enabled:
Then check that archive and packed file scanning is enabled: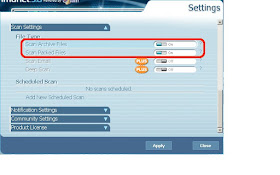 Finally click on "Update Now" to make sure your antivirus database is up-to-date:
Finally click on "Update Now" to make sure your antivirus database is up-to-date: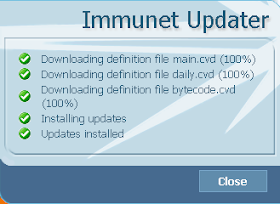
To test the local ClamAV engine you can use the following test file, (which is completely safe, it is not even executable):
Open notepad, then Copy and Paste this text exactly as shown here:
$CEliacmaTrESTuScikgsn$FREE-TEST-SIGNATURE$EEEEE$
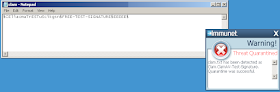
Once you save the file (lets call it clam.txt for example) you should get a popup from Immunet showing that it has detected Clam.ClamAV-Test-Signature:
 You can open the folder you tried to save the file in, and check that it is really gone.
You can open the folder you tried to save the file in, and check that it is really gone.Now you should be confident that you are protected by ClamAV's engine in "Immunet 3.0 powered by ClamAV".
How do you know which engine detected the file?
- if the virusname starts with "W32." then it is a cloud detection
- if it starts with "W32.SPERO.", it is a cloud detection from the SPERO heuristic engin
- if it starts with "W32.ETHOS.", it is a cloud detection from the ETHOS heuristic engine
- if it starts with "W32.Clam.", it is a file that was detected by ClamAV on the cloud
- if it starts with "Clam.", it is a local ClamAV detection
- if it starts with "Clam." and ends with ".UNOFFICIAL", then it is your custom signature
works together with the cloud read on.
A scan can be triggered by:
- on-access, i.e. realtime protection: when you launch an application, copy or move files
- on-demand, via the "Scan Now" button
- scheduled scan, which can be configured in "Scan Settings", "Add New Scheduled Scan
- scans the file using the cloud (by sending the file's fingerprints), if you are online
- if the ClamAV engine is enabled it starts scanning the file, as usual:
- using its (official or custom) signatures database
- scanning files inside archives (if enabled in Settings)
- scanning inside packed executables (if enabled in Settings)
- each of these inner files (inside archives, packed executables) is
- scanned using the cloud as well
- ClamAV checks its local whitelist when it detects a virus
- as soon as either engine finds a malware, scanning is stopped
- the cloud also checks its whitelist for both its own detections and ClamAV's detections
If a malware is detected the file is quarantined, and the malicious process is blocked, prevented from execution.
So you see when you have both the cloud and ClamAV enabled it performs a more thorough scan than when scanning with both individually.
What if a file is detected by both the cloud and the local ClamAV engine?
Currently the detection from the cloud wins, but that may change as we work on optimizing the integration of the engine. Also just because you see a cloud detection, it doesn't mean the local engine wouldn't have detected it.
